In 2025, the cybersecurity landscape is undergoing a seismic shift. The convergence of artificial intelligence (AI), unstructured data proliferation, and increasingly sophisticated threat actors has redefined what constitutes a security breach. No longer confined to isolated incidents, breaches now represent systemic vulnerabilities that can destabilize entire organizations.
Defining the Modern Security Breach
A security breach is an incident where an unauthorized party gains access to an organization’s digital infrastructure, resulting in the compromise, exposure, or theft of confidential information. But in 2025, it’s more than just a cybercriminal slipping past your firewall—it’s about structural vulnerabilities, AI misuse, and the invisible chaos within your data ecosystem.
Whether it’s a single act of unauthorized access or a multi-pronged infiltration, a breach today can spiral into identity theft, large-scale fraud, and catastrophic information theft—sometimes without an alert being triggered.
The Escalating Cost of a Data Security Breach
The cost of a data security breach is no longer just a line item—it’s a full-blown business risk. According to IBM’s 2024 report, the average cost of a security breach reached $4.88 million. Additionally, 1 in 3 breaches now involve shadow data—highlighting how unchecked data proliferation is making it increasingly difficult for organizations to track, govern, and secure their information.
This includes direct costs—ransom payouts, forensic investigations, legal fees—and indirect ones like:
- Regulatory fines for non-compliance
- Loss of customer trust
- Plummeting stock value
- Future investment in security infrastructure
And when breached confidential information ends up on the dark web, the ripple effects can last years—long after headlines fade.
Why the Threat Landscape Has Changed
Today’s security incidents don’t always start with a phishing email. They often emerge from:
- Unstructured data left unmonitored and misclassified
- Over-permissioned access to files containing sensitive financial or customer data
- Forgotten orphaned data that escapes compliance workflows
- Misconfigured cloud storage and data lakes shared beyond intended scopes
- Internal misuse or shadow AI operations handling sensitive content without oversight
These modern-day threats are harder to detect, faster to execute, and frequently enabled by internal blind spots rather than external hacks.
The Silent Risk: Unstructured Data
With more than 80% of enterprise data now unstructured, most breaches target content that isn’t properly categorized, secured, or even visible to IT. Think documents, call recordings, scanned contracts, emails—often containing PII, trade secrets, or intellectual property.
This “invisible data sprawl” is the goldmine for threat actors—and the blind spot for compliance teams.
How Enterprises Are Evolving
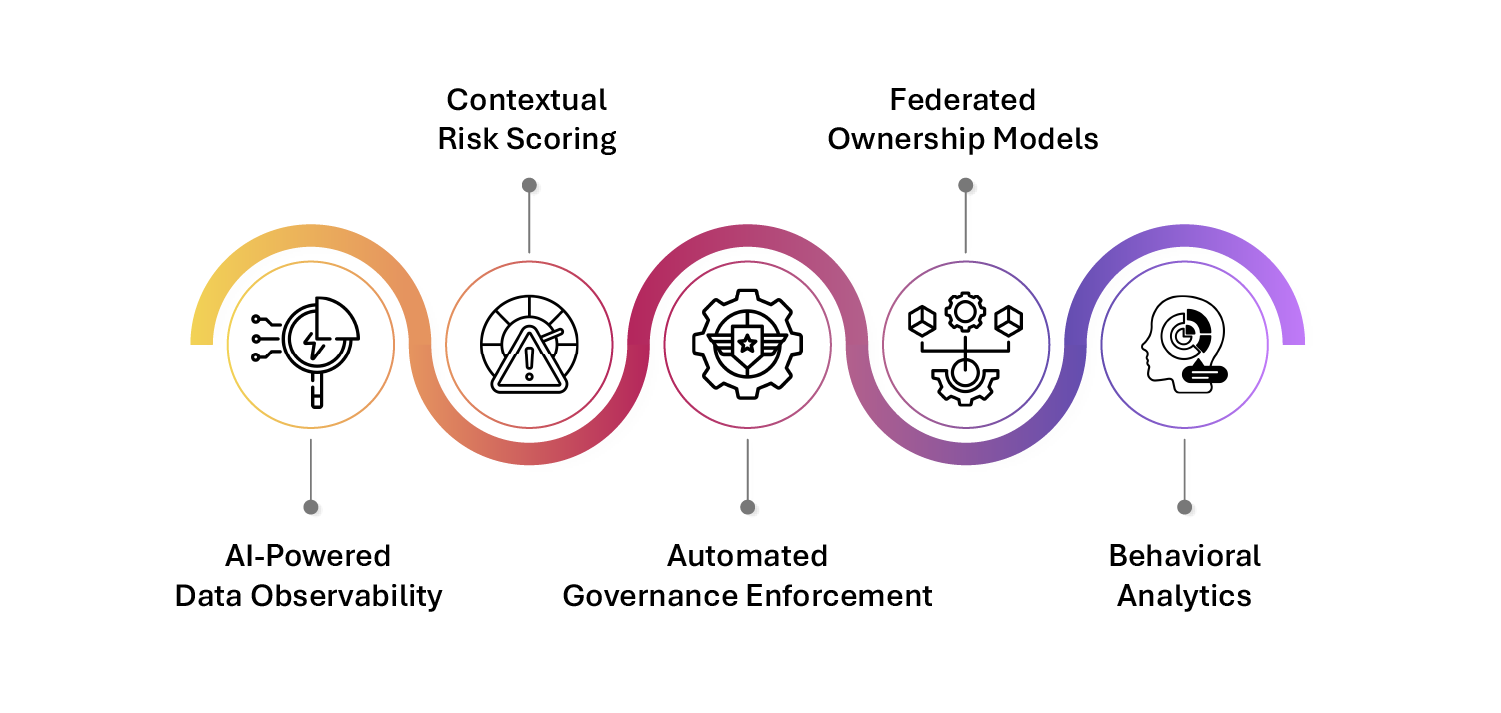
Leading organizations are now shifting from reactive to predictive breach prevention, driven by smart governance and real-time control. Core to this transformation are:
- AI-powered data observability that identifies sensitive data across environments and flags unusual access patterns
- Contextual risk scoring to prioritize threats based on sensitivity, frequency of access, and location
- Automated governance enforcement—ensuring encryption, deletion, and access policies are applied at scale
- Federated ownership models, where data owners—not just IT—control data security decisions
- Behavioral analytics that help uncover potential insider threats before damage occurs
Together, these practices reduce the cost of security breach response and move organizations toward true cyber resilience.
Security Breach Trends to Watch in 2025
- Insider-driven data breaches fueled by misconfigured access or AI misuse
- AI-powered fraud through deepfakes and behavioral spoofing
- Privacy-first regulation escalation, especially around AI and cross-border data flows
- Identity theft surge due to increased credential leaks and dark web exploitation
- Shared responsibility security models where IT, legal, and business leaders collaborate on defense
These developments highlight why enterprises can no longer view security breaches as isolated IT issues—they’re now existential business threats.
In an era where cybercriminals are weaponizing AI and the dark web thrives on stolen confidential information, every organization must treat its data as both an asset and a liability. That means securing it not just from the outside, but understanding where it lives, who has access, and how it’s used—especially as AI models feed on enterprise data to make critical decisions.
The organizations that lead in the future won’t be those with the best perimeter defenses. They’ll be the ones that embed breach prevention into the fabric of their data governance, from endpoint to edge—because in 2025, breach readiness isn’t optional. It’s the new foundation of digital trust.
Getting Started with Data Dynamics:
- Learn about Unstructured Data Management
- Schedule a demo with our team
- Read the latest blog: AI Is Only as Secure as the Data You Feed It. Is Yours Truly Ready?






