What is Data Sharing?
Data Sharing is the practice of distributing or making data accessible to different stakeholders, organizations, or systems, typically for collaboration, analysis, or decision-making purposes. It involves the controlled exchange of data between entities, ensuring that the right people have access to the right data at the right time while maintaining data security, privacy, and compliance with relevant regulations. Effective data sharing enhances collaboration, drives innovation, and enables informed decision-making by allowing parties to leverage shared data insights, while also ensuring that data is protected against unauthorized access or misuse.
Why Is It Important?
Data sharing isn’t just about accessibility—it’s about unlocking the compound intelligence within interconnected ecosystems. In a world where AI, automation, and analytics drive competitive advantage, organizations that operate in isolated data silos risk stagnation. The real power lies in collaborative intelligence, where shared data fuels cross-industry innovation, enhances predictive accuracy and mitigates systemic risks. Imagine healthcare without real-time genomic data exchange or finance without fraud intelligence sharing—entire industries would slow down, operating on incomplete perspectives. The future isn’t just about who owns the most data, but who can securely and intelligently share it to create exponential value without compromising trust and compliance.
Challenges of Data Sharing
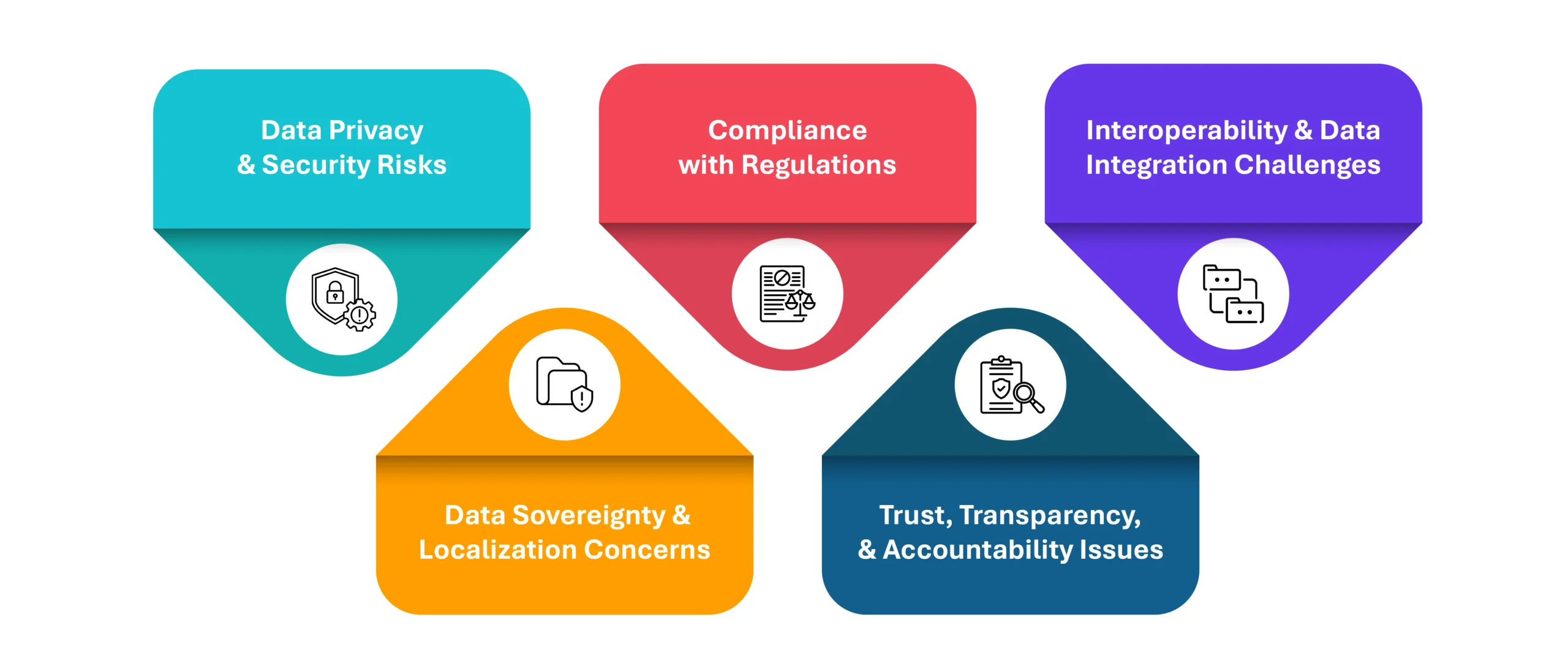
While data sharing has immense benefits, it also presents several challenges, particularly concerning security, compliance, and governance. Below are the key challenges organizations face when implementing data-sharing frameworks:
1. Data Privacy and Security Risks
- Unauthorized Access & Data Breaches: When data is shared across systems, the risk of unauthorized access or breaches increases, especially if robust security measures aren’t in place.
- Insider Threats: Employees or internal users with access to shared data may misuse it, either intentionally or due to negligence.
- Third-Party Vulnerabilities: External partners or vendors may not have the same level of security, making shared data vulnerable to cyberattacks.
2. Compliance with Regulations
- Global Data Protection Laws: Regulations like GDPR, CCPA, HIPAA, and DPDP impose strict rules on how data should be shared, stored, and processed. Organizations need to ensure compliance while maintaining operational flexibility.
- Cross-Border Data Transfers: Countries have different regulations regarding data localization, restricting international data sharing. Businesses operating globally must navigate these complexities to avoid penalties.
3. Interoperability and Data Integration Challenges
- Different Data Formats and Standards: Organizations store data in various formats (structured, semi-structured, unstructured), making seamless data sharing difficult.
- Legacy Systems vs. Modern Infrastructure: Many companies still rely on outdated legacy systems that don’t support modern data-sharing techniques.
- APIs and System Compatibility: Ensuring APIs, databases, and applications can communicate effectively across different platforms is a major hurdle.
4. Data Sovereignty and Localization Concerns
- Jurisdictional Restrictions: Some countries enforce strict data localization laws requiring organizations to store and process data within national borders. This creates challenges for global enterprises needing real-time data access across regions.
- Ownership and Control: Organizations need to establish clear data ownership models that define who has access, who governs data usage, and under what conditions data can be shared.
5. Trust, Transparency, and Accountability Issues
- Lack of Trust Between Entities: Organizations may be hesitant to share data due to concerns about misuse, intellectual property theft, or competitive disadvantages.
- Data Quality and Accuracy: If shared data is outdated, incomplete, or inconsistent, it can lead to incorrect business insights and flawed decision-making.
- Lack of Visibility into Data Usage: Without proper tracking and auditing mechanisms, organizations may struggle to monitor how shared data is being used and whether it complies with governance policies.
5 Best Practices for Secure and Compliant Data Sharing
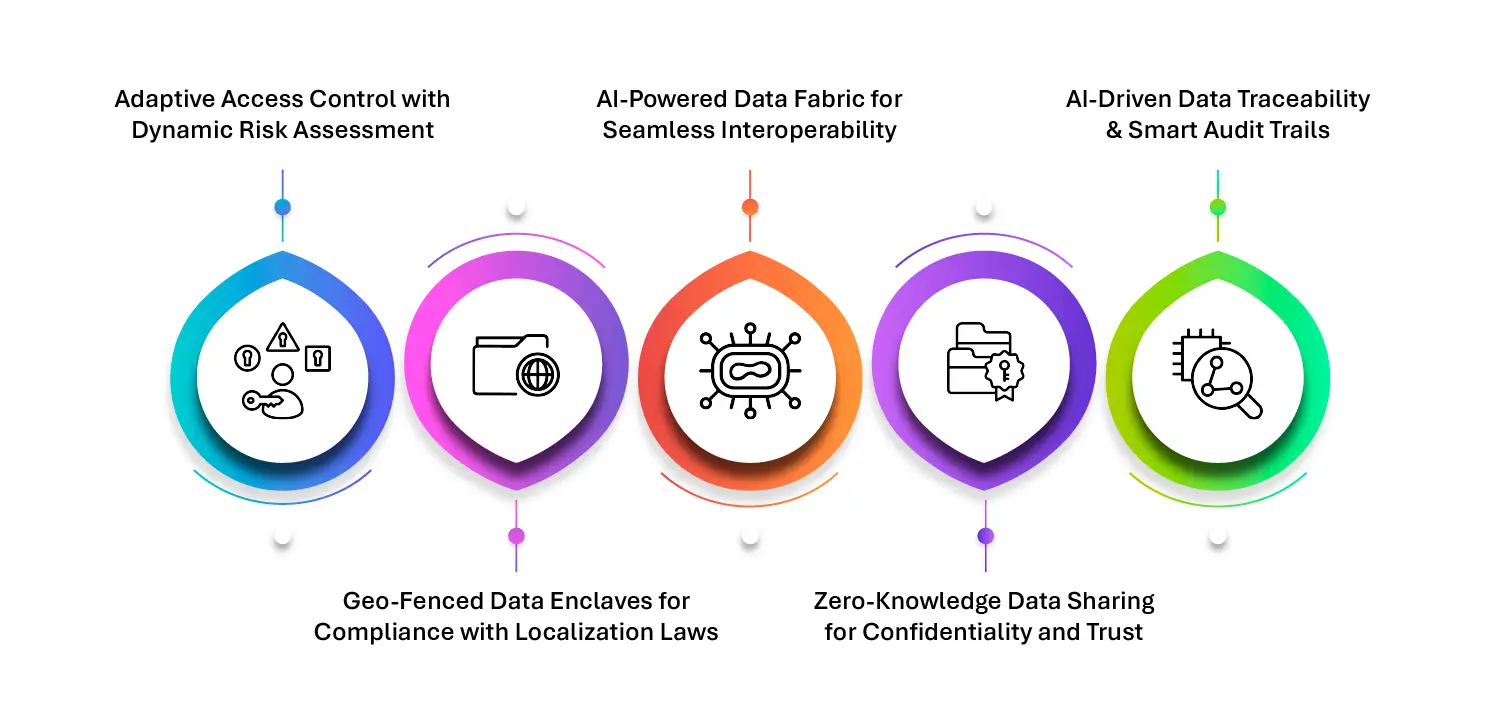
- Adaptive Access Control with Dynamic Risk Assessment: Traditional role-based access controls are no longer enough. Implementing adaptive access control (AAC) with real-time risk assessment ensures that data access is constantly evaluated based on user behavior, device security, and location. If an employee logs in from an unverified device or an unusual location, access can be automatically restricted or require additional verification. This proactive approach minimizes the risk of insider threats and unauthorized breaches by dynamically adjusting access privileges based on evolving security conditions.
- Geo-Fenced Data Enclaves for Compliance with Localization Laws: Cross-border data sharing becomes complex with different localization laws. Using geo-fenced data enclaves within sovereign cloud solutions allows organizations to store and process data within specific legal jurisdictions while still enabling controlled global access. Unlike traditional data localization, this method ensures compliance with regional regulations without disrupting international operations, striking a balance between legal requirements and business agility.
- AI-Powered Data Fabric for Seamless Interoperability: Organizations often struggle with sharing data across different formats, legacy systems, and modern cloud platforms. AI-driven data fabric solutions act as a middleware layer, automatically mapping, translating, and normalizing data for seamless sharing. This eliminates the need for extensive infrastructure overhauls and ensures compatibility between structured, semi-structured, and unstructured data. Businesses can integrate data across multiple platforms effortlessly, improving collaboration and decision-making.
- Zero-Knowledge Data Sharing for Confidentiality and Trust: Sharing data with third parties always carries risks, but zero-knowledge data-sharing protocols offer a solution. Techniques like secure multi-party computation (SMPC), differential privacy, and homomorphic encryption allow organizations to analyze and exchange insights without exposing raw data. This protects intellectual property, prevents competitive misuse, and ensures regulatory compliance, fostering trust between entities while keeping sensitive data secure.
- AI-Driven Data Traceability and Smart Audit Trails: Tracking data usage is critical for security and compliance. AI-powered traceability tools continuously monitor data access, modifications, and transfers, creating real-time audit trails that are immutable and verifiable. Blockchain-based logging adds another layer of protection, ensuring that every action on shared data is transparent and tamper-proof. AI can also detect anomalies, such as unusual access patterns or unauthorized data exports, allowing organizations to prevent security breaches before they happen.
Getting Started with Data Dynamics:
- Learn about our Unstructured Data Management Software – Zubin
- Schedule a demo with our team
- Read the latest blog: Unstructured Data: The Blind Spot CISOs and CIOs Must Solve—Together






