CISOs have always known that cybersecurity is a moving target. But in 2025 and beyond, the rules of engagement are being rewritten. AI-powered threats are no longer just a looming possibility—they’re here, evolving in real-time, exploiting vulnerabilities faster than legacy defenses can react. The conversation has long been focused on fortifying the perimeter, but the real battle lies within. Deepfakes, autonomous hacking, and AI-driven exploits may dominate headlines, but the real question is: how secure is enterprise data from the inside out the real battle starts within—by fortifying internal data policies.
The Growing Risk: When Data Mismanagement Becomes a Security Breach
Add to that the sheer volume of ungoverned data generated within enterprises—emails, contracts, financial records, customer information, and proprietary research. By 2025, global data creation is expected to surpass 180 zettabytes, yet over 50% of enterprise data remains dark—unclassified, unstructured, and largely unmanaged. This dark data, coupled with fragmented governance, creates a perfect storm for cyber threats.
For instance, in the Middle East, where digital transformation is accelerating across sectors like banking, energy, and government, the risk is even greater. With cybercrime expected to cost the region over $2.5 billion annually, regulatory frameworks such as the UAE’s Personal Data Protection Law (PDPL) and Saudi Arabia’s National Cybersecurity Strategy are driving stricter data accountability. But in an era where AI-driven attacks evolve 300% faster than traditional security measures, compliance alone is no longer enough.
Attackers are no longer just breaching firewalls; they are weaponizing AI to exploit ungoverned data—turning forgotten files, outdated credentials, and misconfigured cloud environments into high-value attack vectors. Future-ready CISOs must go beyond passive data storage to intelligent data governance, using AI not just for defense, but for real-time classification, anomaly detection, and policy enforcement Because in the era of autonomous threats, the organizations that understand their data will be the only ones that can truly protect it.
The AI Threat Landscape in 2025: Why Internal Data Governance Is Now Mission-Critical
AI has shifted from an innovation tool to a cyber weapon. By 2025, AI-driven attacks will cause $10.5 trillion in annual damages, outpacing traditional security. Attackers now leverage AI for automated reconnaissance, hyper-realistic phishing, and large-scale data exploitation. Here’s how AI is reshaping the threat landscape:
- Self-Learning AI Attacks – AI-powered malware can now study an organization’s data flows, employee behaviors, and access patterns in real-time, crafting precision-targeted intrusions that evade traditional detection. An MIT study found AI-driven breaches occur 30% faster than human-led threats.
- Data Poisoning – Adversaries infiltrate unprotected datasets, subtly manipulating AI models used in finance, healthcare, and security. Gartner predicts that by 2026, 30% of AI cyberattacks will involve data poisoning, model theft, or adversarial manipulations, directly compromising decision-making systems.
- Deepfake and Voiceprint Attacks – AI-generated deepfakes are now 99% indistinguishable from real interactions, leading to an explosion in executive impersonation fraud. In 2023 alone, voice cloning scams resulted in $1.3 billion in corporate losses, and this number is expected to quadruple by 2026 as threat actors refine their methods.
- AI-Driven Ransomware – Cybercriminals no longer rely on manual encryption methods; instead, they deploy AI to autonomously identify critical data, encrypt it, and negotiate ransom terms dynamically.
Internal Data Policies: The Foundation of AI-Resilient Security
CISOs can no longer rely solely on perimeter defense in the face of AI-powered threats, which are expected to cause $10.5 trillion in damages annually by 2025. AI-powered cyber threats exploit internal data mismanagement at an exponential scale, making data governance the new frontline of cybersecurity. A well-orchestrated internal data policy doesn’t just mitigate threats—it transforms enterprise security into a self-regulating, AI-augmented ecosystem.
Here’s how AI-driven internal data governance becomes an organization’s first and most effective layer of defense:
- Autonomous Data Classification & Risk Prioritization – Traditional data classification struggles to keep pace with the 2.5 quintillion bytes of data created daily. AI-powered solutions now continuously scan, label, and prioritize data in real-time, based on content, sensitivity, and usage patterns. By automatically categorizing both structured and unstructured data, security teams gain instant visibility into their most vulnerable assets, reducing risk exposure by 40%.
- AI-Driven Threat Intelligence & Risk Mitigation – Attackers use AI to probe and predict weaknesses. Organizations must counter this by deploying AI-driven threat intelligence models that map access behaviors, detect deviations, and neutralize unauthorized attempts before they escalate. AI can simulate potential attack paths based on past incidents, providing CISOs with actionable foresight to reinforce weak points before adversaries exploit them.
- Proactive Insider Threat Detection & Zero-Trust Reinforcement – With 70-80% of data breaches originating from internal sources- whether through negligence, misconfigurations, or malicious insider activity. AI is pivotal in reinforcing zero-trust security. Through AI-powered behavioral analytics, organizations can continuously monitor user actions, flagging abnormal data interactions and dynamically adjusting access based on real-time intent and context, ensuring access is granted only when necessary.
- AI-Powered Data Hygiene & Automated Governance – AI-powered data hygiene and automated governance are essential in managing the growing volume of unstructured data, which is often redundant, outdated, or poorly managed, creating prime targets for AI-driven ransomware attacks. By 2025, over 80% of corporate data will be unstructured, and 30% of it will be redundant or obsolete. AI-driven automation continuously scans and identifies unnecessary data, automating the process of encryption, archiving, or purging it in real time. This proactive approach reduces exposure by up to 45%, minimizing vulnerabilities in the organization’s data architecture and significantly lowering the risk of exploitation.
- Intelligent Compliance Enforcement & Continuous Audit Readiness – Compliance requirements are evolving at an unprecedented pace, with strict regulations like India’s DPDP Act, Saudi Arabia’s PDPL, and the UAE’s cybersecurity mandates demanding real-time data accountability. By 2025, global spending on compliance is expected to surpass $13 billion as businesses scramble to meet new standards. This is where AI-driven automation becomes a game changer. By embedding policy-driven controls directly into data workflows, AI eliminates the need for manual audits, cutting audit prep time by 40%. In fact, organizations leveraging AI for compliance report 50% fewer regulatory penalties, as it constantly monitors and adapts data policies to meet ever-evolving requirements. As new regulations like the EU’s DORA come into play, AI will be essential for staying ahead of regulatory scrutiny while reinforcing overall security.
Internal data governance is no longer just a defensive measure—it’s a proactive, AI-augmented security strategy that adapts in real time, minimizing human effort while maximizing resilience. By embedding AI-powered internal data policies, CISOs can shift from reactive firefighting to predictive, automated risk mitigation—turning unstructured data from a liability into a strategic asset.
The Future of Data Security: Why CISOs Must Leverage AI-Powered Data Policy Frameworks
As enterprises expand, the explosion of unstructured data introduces mounting security, compliance, and governance challenges. Traditional security models struggle to keep pace, leaving organizations vulnerable to data breaches, regulatory penalties, and inefficiencies. To stay ahead, CISOs must adopt AI-powered data policy frameworks that automate governance, secure unstructured data, and mitigate risks proactively. These frameworks bring real-time intelligence, predictive security, and policy-driven automation, ensuring enterprises can maintain control, compliance, and efficiency at scale.
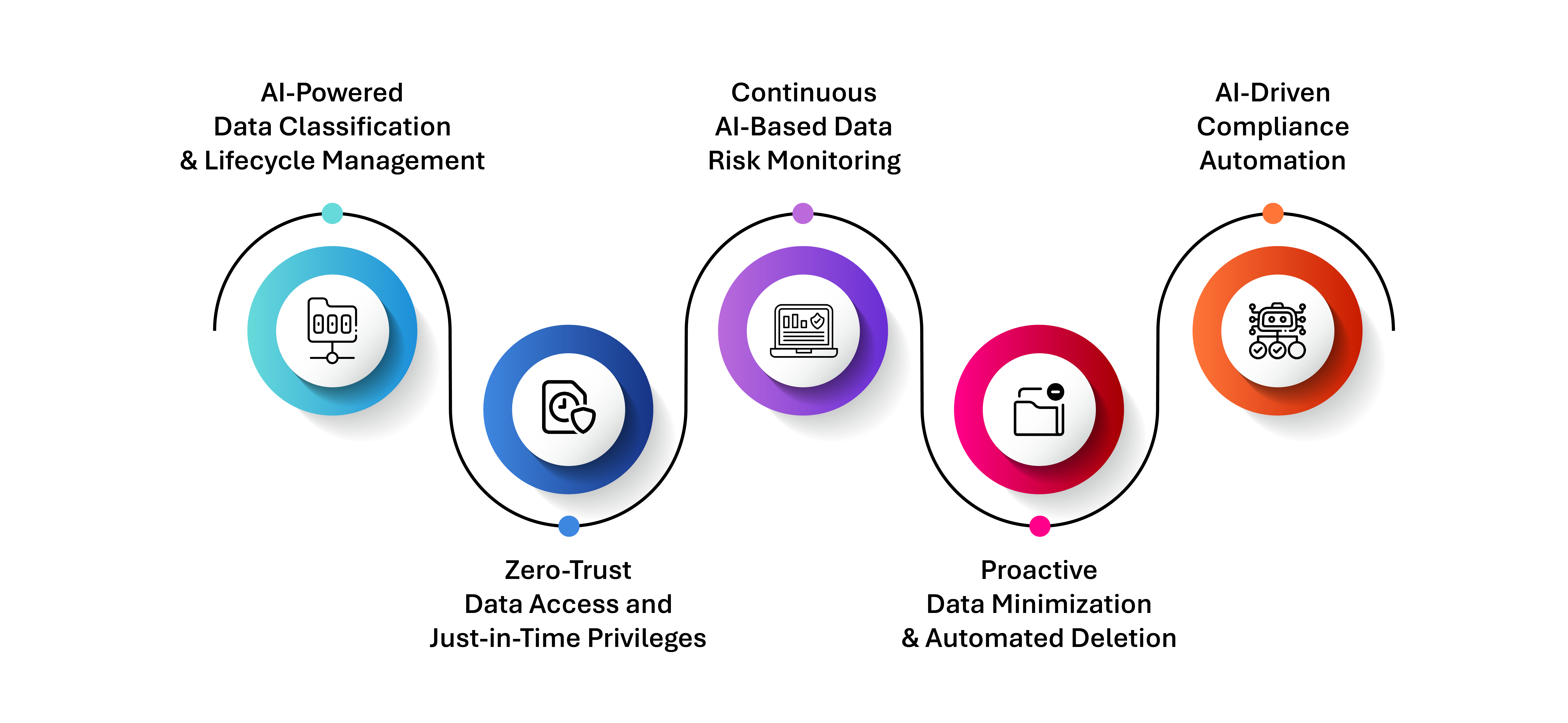

1️. AI-Powered Data Classification & Lifecycle Management
Managing unstructured data at scale is impossible without visibility. AI-driven classification tools automatically discover, tag, and categorize data, identifying sensitive, redundant, and obsolete information across hybrid environments. This prevents data silos, regulatory blind spots, and compliance risks, while lifecycle management automates retention, archival, and deletion processes. With policy-driven governance, enterprises can eliminate over-retention, prevent shadow IT, and enforce data hygiene, ensuring that only relevant, secure, and compliant data remains in active use.
2️. Zero-Trust Data Access & Just-in-Time Privileges
Static role-based access models expose enterprises to privilege misuse, insider threats, and excessive permissions. AI-powered Zero-Trust security enforces real-time, identity-based access policies, granting users only the permissions required for their current task. Just-in-Time (JIT) privilege escalation prevents privilege creep and unauthorized access, while behavior analytics detect suspicious access patterns and enforce dynamic restrictions. This ensures the principle of least privilege (PoLP) is upheld, reducing the risk of data exposure without disrupting productivity.
3️. Continuous AI-Based Data Risk Monitoring
Cyber threats evolve rapidly, but traditional security tools rely on static rules and delayed alerts, allowing attacks to go undetected. AI-driven risk monitoring continuously scans user activity, access logs, and file movements, flagging unauthorized access, anomalous behavior, and potential exfiltration in real time. Machine learning models assign risk scores, helping security teams prioritize threats and take preemptive action before breaches occur. By integrating AI into security operations, organizations shift from reactive incident response to proactive risk mitigation, reducing overall exposure.
4️. Proactive Data Minimization & Automated Deletion
Data hoarding not only increases storage costs and operational inefficiencies but also expands the attack surface. AI-driven governance frameworks enforce intelligent retention policies, automatically identifying and eliminating redundant, outdated, and trivial (ROT) data while ensuring compliance with global regulations like GDPR, CCPA, and HIPAA. By automating archival and deletion, enterprises reduce legal liabilities, security risks, and unnecessary data sprawl, keeping their information ecosystems lean, secure, and compliant.
5️. AI-Driven Compliance Automation
Compliance management is traditionally manual, time-consuming, and error-prone, making regulatory adherence a constant challenge. AI-powered compliance automation streamlines governance by enforcing security policies in real-time, generating automated audit reports, and continuously monitoring for violations. This eliminates human error, regulatory gaps, and audit complexities, allowing organizations to maintain a robust security posture with minimal overhead. With real-time policy enforcement, businesses can confidently navigate global compliance mandates without operational disruptions.
The Shift from Cyber Defense to Data Governance Leadership
CISOs must drive a paradigm shift in 2025: security starts at the data layer. AI-driven threats are inevitable, but organizations that take control of their data at the foundational level will gain asymmetric defense advantages.
By enforcing AI-powered data classification, zero-trust data governance, and continuous risk-adaptive security, companies can automate risk reduction at scale. This does not eliminate external threats, but it denies them opportunities. When data hygiene is high, attack surfaces shrink. When internal misconfigurations are fixed, AI-driven threats lose precision. When compliance is embedded into real-time security, the regulatory burden decreases.
This is where Data Dynamics’ Zubin becomes a game-changer. Zubin is an AI-powered self-service data management software that directly addresses the first layer of defense by offering intelligent data governance, real-time risk assessment, and automated policy enforcement. Unlike traditional security tools that focus on perimeter defenses or compliance, Zubin integrates data security with AI-driven governance, ensuring that organizations have full control over their unstructured data environments.
How does Zubin strengthen enterprise security?
- AI-Driven Data Intelligence: Zubin analyzes, classifies, and tags unstructured data at scale, eliminating dark data and reducing the attack surface that AI-driven threats exploit.
- Automated Data Lifecycle Management: Organizations can define data retention, deletion, and access policies with zero manual intervention, ensuring that security is embedded in daily operations rather than being an afterthought.
- Risk-Aware Data Mobility: With enterprises moving data across hybrid and multi-cloud environments, Zubin enables secure, policy-driven data migration, ensuring that sensitive information remains protected even as it moves across platforms.
- Compliance as a Byproduct of Security: By aligning data governance with security-first principles, Zubin makes regulatory compliance seamless, transforming it from a burden into an automated, risk-driven process.
The result? A fortified first layer of defense that strengthens everything else. When organizations have full visibility and control over their data, they eliminate security blind spots, reduce regulatory complexity, and ensure that AI-powered threats have fewer opportunities to exploit weaknesses.
CISOs who recognize that data governance is security’s linchpin will lead the way in 2025. With Zubin as a strategic enabler, enterprises can shift from reactive security to proactive, AI-powered data resilience—turning their most significant cybersecurity challenge into a competitive advantage.
To explore how Zubin can transform your enterprise’s approach to data security, governance, and compliance, click here.