Pharmaceutical enterprises face a unique set of challenges when it comes to protecting sensitive data. With increasing amounts of data stored and transferred, the risk of data sprawl and cyber security threats is ever-present. The risk extends beyond simply losing valuable customer information—there are legal and cost implications as well. For instance, according to the 2021 Cost of a Data Breach Report by the Ponemon Institute, the average total cost of a single breach in the healthcare industry in 2021 was $9.23 million.
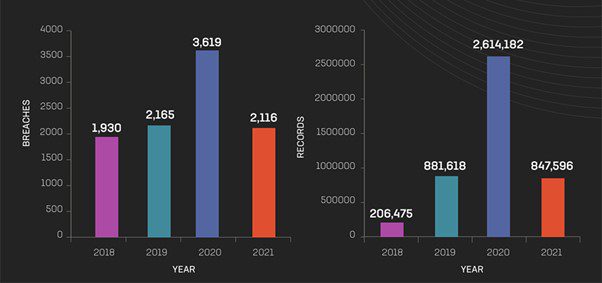
Year-over-year breaches and exposed records

This blog post will explore what pharmaceutical companies can do to combat data sprawl and protect critical information from malicious actors. From best practices for structuring and analyzing data to secure storage solutions and more, read on to learn how your business can stay ahead of cybersecurity threats in an increasingly digital world.
The Data Sprawl Challenges Facing Pharmaceutical Enterprises
Data sprawl is a major problem for pharmaceutical enterprises. It results in the accumulation of large amounts of data in different silos across the organization, making it difficult to access and use. This can lead to problems with data quality and integrity, as well as security risks.
There are several causes of data sprawl in pharmaceutical enterprises. One is the increasing use of electronic health records (EHRs). EHRs are often stored in different formats and locations, making it difficult to consolidate and access them. Another cause is the proliferation of clinical trials. Clinical trials generate a lot of data that is often spread across different databases and systems.
Here are some common types of data sprawl that can occur in pharma companies:
- Redundant data: This occurs when multiple copies of the same data exist in different locations, leading to inefficiencies in storage and management.
- Unstructured data: This includes data in the form of documents, emails, and other unstructured formats that are difficult to organize and manage.
- Dark data: This refers to data that is collected but not analyzed or used, leading to wasted storage and processing resources.
- Shadow IT: This occurs when employees use unauthorized software or applications to store or process data, leading to data being scattered across different systems and creating a security risk.
- Unmanaged data growth: This happens when the volume of data in the organization grows rapidly without proper planning or management, leading to inefficiencies and security risks.
- Lack of data lifecycle management: This refers to the absence of a clear strategy to manage data throughout its lifecycle, from creation to disposal, leading to data being stored and managed inefficiently.
- Data incompatibility: This occurs when data is stored in incompatible formats, making it difficult to integrate and analyze data across different systems.
The problem of data sprawl can be addressed by implementing a centralized data management system. This system should be designed to store all data in a single location and format. It should also be accessible to all users across the organization.
The Cyber Security Challenges Facing Pharmaceutical Enterprises
Pharmaceutical enterprises face a range of cybersecurity challenges that put their sensitive data, intellectual property, and reputation at risk. These challenges include attacks from state-sponsored hackers seeking to steal confidential information and disrupt operations, as well as attacks from criminal organizations looking to profit from stolen data. Additionally, pharmaceutical enterprises must protect against insider threats, such as employees accessing or stealing sensitive data, and must ensure the security of their supply chain partners, who may be targeted as a way to access the enterprise’s network. The widespread use of connected medical devices and the growth of telemedicine also introduce new security risks, as these technologies can be targeted by cybercriminals seeking to exploit vulnerabilities in the devices and networks.
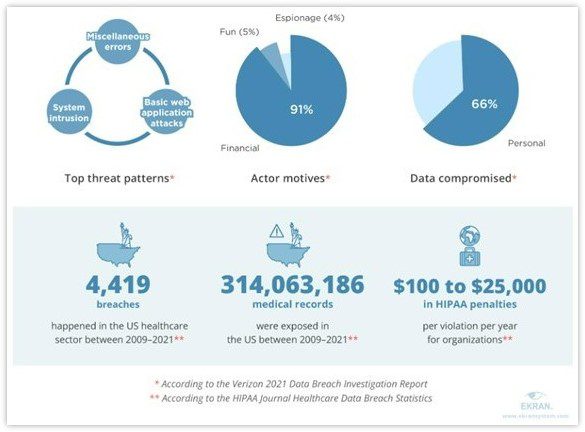
A recent report published by cybersecurity firm Constella Intelligence, based in Los Altos, California, analyzed data exposures, breaches, and leakages in the industry between January 2018 and September 2021. The company discovered over 9,030 breaches or leakages during this period and more than 4,500,000 exposed records. These records contained sensitive information, including passwords and financial data.
Additionally, In January 2021, a HIPPA-covered entity reported the exposure of the personal information of 3.5 million people. For a number of years, hackers had access to this protected health information. By exploiting the breached health plans of the Corporation, they managed to steal highly sensitive data, including consumers’ financial information, social security numbers, and other confidential details.
Cyberthreats in the Pharmaceutical and Healthcare Industry

This just goes to prove that Data mismanagement and sprawl are the ticking time bomb of pharmaceutical breaches. In a recent study, Tufts CSDD revealed that Phase III clinical trials generate an average of 3.6 million data points, three times more than 10 years ago. Just imagine the operational disruption if all this data is breached! As seen in an incident in 2017, Merck & Co. (NYSE: MRK) could not meet the high demand for its hepatitis B vaccine due to being targeted by Notpetya ransomware. The result? A colossal estimated loss of $1.4 billion!”
Some of the key cyber security challenges facing pharmaceutical enterprises include:
- Intellectual property theft: Pharmaceutical companies hold valuable intellectual property in the form of patents, research data, and confidential business information. This makes them a prime target for cybercriminals seeking to steal this valuable information for financial gain.
- Ransomware attacks: Ransomware attacks are increasingly common in the healthcare industry, including pharmaceutical companies. These attacks can disrupt operations and cause significant financial losses.
- Insider threats: Insider threats, whether intentional or unintentional, can result in the exposure or theft of sensitive data. Employees, contractors, and vendors with access to sensitive data pose a significant risk.
- Third-party vendor risk: Pharmaceutical companies often work with third-party vendors, such as contract research organizations and clinical trial sites, which can introduce additional cyber security risks.
- Increasingly sophisticated attacks: Cyber criminals are constantly developing new attack methods, including advanced persistent threats, social engineering, and zero-day exploits, which can be difficult to detect and prevent.
- Legacy systems: Many pharmaceutical companies rely on legacy systems that may not be up to date with the latest security patches, leaving them vulnerable to known vulnerabilities.
Cybersecurity threats are constantly evolving, and pharmaceutical companies must stay ahead of the curve to protect their data. They need to start by structuring unstructured data and getting granular level insights into their data, followed by having strong cyber security policies and procedures in place and educating their employees on how to avoid becoming victims of cyber-attacks.
A Guide to Protecting Sensitive Data
A recent IBM study shows that over 80% of all data is dark and unstructured. Dark data can be a significant contributor to cyber risk for organizations. This is because dark data, which is unstructured and often stored in less visible or accessible locations, can be more vulnerable to unauthorized access, theft, or misuse. The lack of visibility into this data and its location can make it more challenging to identify and protect sensitive information, leaving organizations open to data breaches and other cyber threats. Dark data can include legacy data, backups, and other types of data that may no longer be in active use but can still contain valuable information that can be exploited by malicious actors. The unstructured nature of this data can make it more difficult to secure through traditional cybersecurity measures, such as firewalls and access controls. By gaining a better understanding of their dark or unstructured data, organizations can identify potential security threats and take appropriate measures to protect their sensitive information.
Effective unstructured/dark data management practices include:<
- Identification and Classification: Dark data can be identified and classified based on its type, source, and relevance to the organization, allowing for a more accurate assessment of the cyber risk.
- Inventory and Location: Dark data can be inventoried, and its location determined, allowing for better data control and monitoring. It can help detect any anomalies or unauthorized activity that may indicate a data breach or misuse of sensitive data.
- Access Control and Encryption: Access to dark data can be controlled and limited to authorized individuals, and encryption can protect sensitive data both at rest and in transit, ensuring that it is protected from unauthorized access, tampering, and theft.
- Retention and Disposal: Dark data can be retained only for the necessary time period and securely disposed of when it is no longer required, reducing the risk of exposure or misuse of data. Data purging can help ensure that sensitive data is securely deleted once it is no longer required, reducing the risk of exposure or misuse of data.
- Data Backup and Recovery: Regular backups and disaster recovery plans can ensure that sensitive data is not lost in the event of a breach or disaster.
- Data Governance: Increasing oversight and intelligence about data at risk can ensure that sensitive data is used only for authorized purposes, such as research or business operations, and not for personal or malicious purposes. Additionally, sensitive data can be protected in accordance with privacy regulations and best practices, reducing the risk of privacy violations and reputational damage.
By effectively managing unstructured/dark data, organizations can reduce the risk of cyber attacks, data breaches, and reputational damage. With a comprehensive understanding of the data they hold, organizations can improve their cybersecurity posture, reduce their attack surface, and ensure that sensitive data is protected.
Implementing a Data Protection Strategy
When it comes to data protection, pharmaceutical enterprises face unique challenges. They must comply with regulations like the Health Insurance Portability and Accountability Act (HIPAA) and the European Union’s General Data Protection Regulation (GDPR) while also safeguarding sensitive information from cyber threats.
To tackle these challenges, pharmaceutical enterprises must implement a comprehensive data protection strategy. Here’s a 7-pronged approach that enterprises that’s sure to help:
- Identify and categorize data: Identify the types of data the organization handles, where it is stored, and who has access to it. Classify data according to its sensitivity and criticality using metadata and content analytics.
- Assess risks and threats: Assess the risks and threats that may impact the organization’s data, such as cyberattacks, human error, natural disasters, and supply chain disruptions.
- Define data protection policies: Develop policies and procedures that outline how the organization will protect its data. Policies should cover access controls, data classification, data retention, and disposal, incident response, and employee training.
- Select data protection solutions: Choose data protection solutions that align with the organization’s policies and requirements. This may include firewalls, intrusion detection & prevention systems, encryption, access control systems, backup & recovery systems and unified data management software.
- Implement and monitor data protection measures: Deploy the selected data protection solutions and implement policies and procedures. Regularly monitor and test the effectiveness of data protection measures and update them as needed to address new threats and risks.
- Educate and train employees: Educate and train employees on the importance of data protection and how to adhere to the organization’s policies and procedures. This can include cybersecurity awareness training, phishing simulations, and role-based training.
- Review and improve the strategy: Regularly review the data protection strategy to ensure it remains effective and up to date. This can include risk assessments, testing, and incident response simulations.
Conclusion
Data sprawl and cyber security challenges in pharmaceutical enterprises are a real threat that needs to be addressed. By implementing a unified data management platform, organizations can better protect their sensitive data and reduce the risk of becoming victims of malicious attacks.
The Data Dynamics unified data management platform is an effective solution that can assist pharmaceutical organizations in maximizing the value of their unstructured and high-volume data while ensuring that robust security measures are in place to prevent data breaches. The platform achieves this by centralizing data, identifying personally identifiable information (PII/PHI), and improving security controls like data remediation, data quarantining, access control management, and immutable audit logging. This helps organizations to manage their enterprise data efficiently while maintaining the integrity of their data. Overall, the Data Dynamics unified data management platform is an excellent solution for pharmaceutical organizations that want to improve their data management practices, prevent data breaches, and ensure that their sensitive data is well-protected.
To know more about Data Dynamics’ Security suite, please visit – https://www.datadynamicsinc.com/security/ or contact us at solutions@datdyn.com I (713)-491-4298.