- In an age defined by data proliferation, the critical importance of robust PII (Personally Identifiable Information) management to safeguard individual privacy and data security cannot be overlooked.
- The recent fallout in the UK regarding PII mismanagement, led by Nigel Farage, further highlights the importance of this issue.
- While enterprises across the globe battle with efficient PII management, especially due to challenges related to data volume, disparate sources, and unstructured data, they have no choice but to rise to the occasion and cater to consumer demands of data democratization.
- Unified and effective data management is the game changer helping organizations achieve the right balance between control, custodianship, and empowerment.
In an age defined by the proliferation of data, the significance of effective data management cannot be overstated. The recent news surrounding Nigel Farage’s Subject Access Request (SAR) sheds light on the crucial role of PII (Personally Identifiable Information) management in safeguarding individual privacy and data security. This blog explores the critical importance of robust PII management, the need for data democratization to empower individuals with control over their data, and the role of comprehensive big data management in ensuring the responsible and secure use of information.
Understanding PII: Key Role in Data Management
So, what’s this all about? Nigel Farage, a well-known political figure, exercised his right to a SAR, seeking access to his personal data (PII) that was held by a certain organization. A Subject Access Request (SAR) is a powerful tool that empowers individuals to access information about their own personal data that organizations hold. It plays a pivotal role in data protection laws, including the General Data Protection Regulation (GDPR) in the European Union and similar regulations in various other regions. The GDPR is a comprehensive data protection regulation that came into effect in 2018. It places stringent requirements on organizations that process the PII of EU residents, regardless of where the organization is located. The GDPR emphasizes transparency, informed consent, data minimization, and the right to access and delete personal data. Non-compliance can result in fines of up to 4% of global annual revenue or €20 million, whichever is higher. Similarly, the CCPA, which became effective in 2020, aims to enhance privacy rights and consumer protection for California residents. It grants individuals the right to know what personal information is collected about them, the right to opt out of the sale of their information, and the right to request the deletion of their data. Non-compliance can lead to significant financial penalties.
These regulations are just two examples of a growing global trend toward strengthening data protection and PII management. They help individuals their right to be informed about how their Personally Identifiable Information (PII) is being processed and to obtain access to this data when requested. The primary goal here is to hand individuals greater control over their personal data, allowing them to comprehend how organizations use, store, and share their information.
Now, let’s address the elephant in the room – why is PII so important in data management? Well, PII refers to any data that can identify you – your name, address, financial details, and more. Basically, it’s the digital equivalent of your personal diary. Protecting this information is vital for ensuring your privacy and safeguarding against potential data breaches and regulatory frameworks like GDPR and CCPA play a crucial role in guiding organizations in handling PII responsibly. After all, no one wants their private life splashed all over the internet! Here’s a closer look at the potential risks and repercussions:
Managing PII: Assessing Risks and Consequences
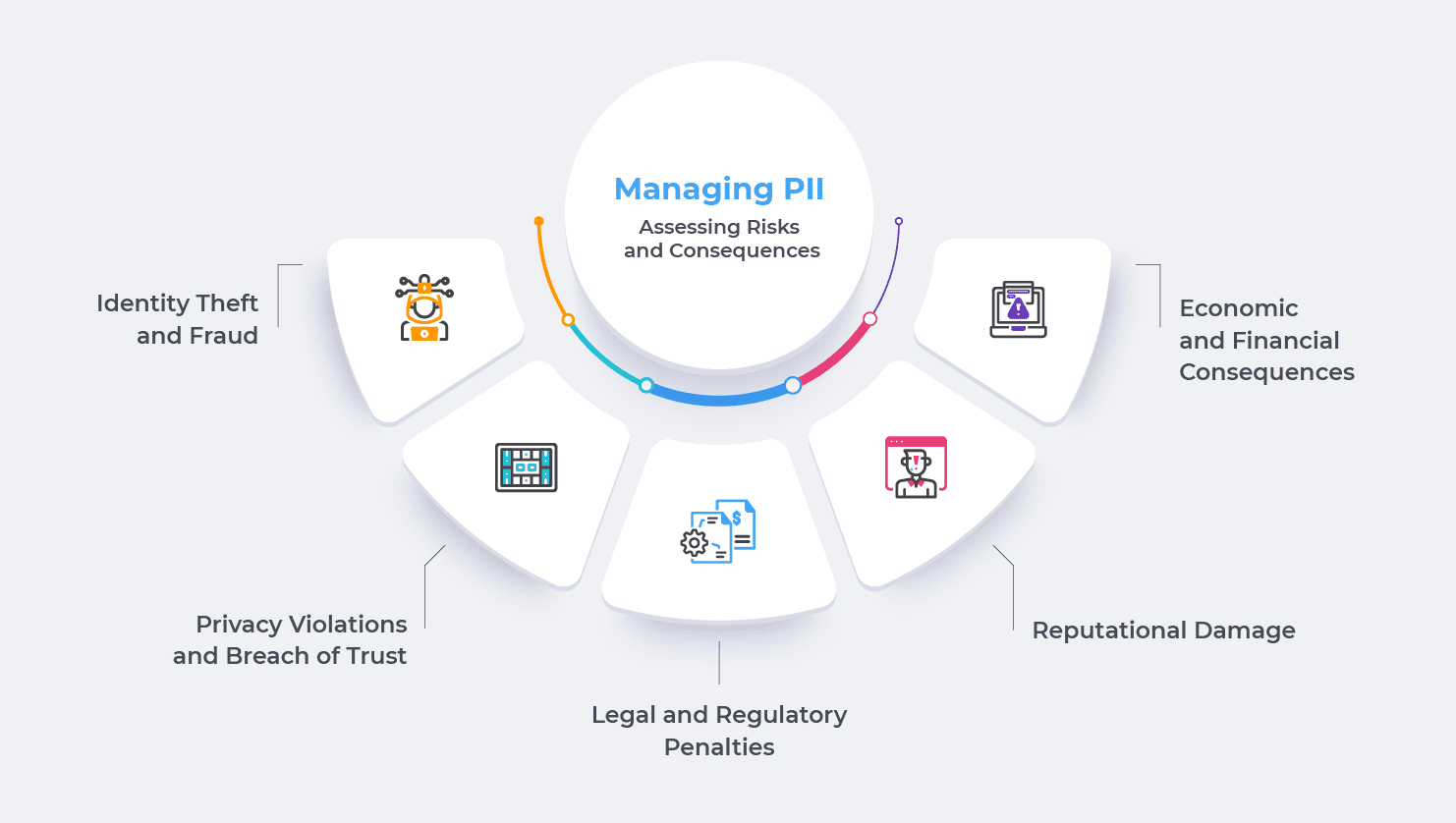

- Identity Theft and Fraud: So, you know how your personal information like your Social Security number, birth date, and address is valuable, right? Well, if someone gets their hands on that data, they could use it for identity theft and fraud. Remember the Equifax data breach in 2017? It exposed PII of about 147 million Americans, and it was a total disaster. Many people suffered financial losses and had their reputation tarnished due to identity theft.
- Privacy Violations and Breach of Trust: Imagine you trust a company with your personal data, but they end up mishandling it. That’s exactly what happened with Facebook and Cambridge Analytica. The firm improperly harvested PII from millions of Facebook users without their consent, and that was a huge breach of trust. People felt violated and questioned Facebook’s commitment to their privacy.
- Legal and Regulatory Penalties: When organizations fail to protect PII properly, they can face serious consequences. Just look at British Airways – they got hit with a hefty £183 million fine by the UK’s Information Commissioner’s Office for a data breach that affected 500,000 customers. Ouch! That kind of financial penalty is enough to put any company in a tough spot.
- Reputational Damage: Public reputation can make or break a company? Well, mishandling PII can lead to a PR nightmare. Take Uber, for instance. They tried to cover up a data breach that exposed the PII of 57 million users, and boy, did that backfire. People lost trust in Uber, and it took them a while to rebuild their reputation.
- Economic and Financial Consequences: Let’s talk money. A data breach is no small thing. According to a study, the average cost of a data breach in 2020 was a whopping $3.86 million! That includes all the expenses for investigating, responding, legal actions, and the hit to their reputation. It’s not just individuals who suffer; the economy as a whole can take a hit when data is mismanaged.


PII data management is undeniably crucial for organizations, but why is it increasingly becoming a challenge? Why do enterprises find it hard to meet consumer demands for data democratization? And why are they struggling to instill faith and trust among data owners by securing their information? One potential answer lies in the realm of unstructured data. As much as 80% of enterprise data today is unstructured, scattered, and left unprotected. Deciphering and safeguarding these data sprawls seem like insurmountable tasks for enterprises. Let’s delve into some of the most significant challenges that enterprises continually face and explore potential solutions to overcome these obstacles.
Navigating PII Management: Avoiding Six Pitfalls with Six Solutions
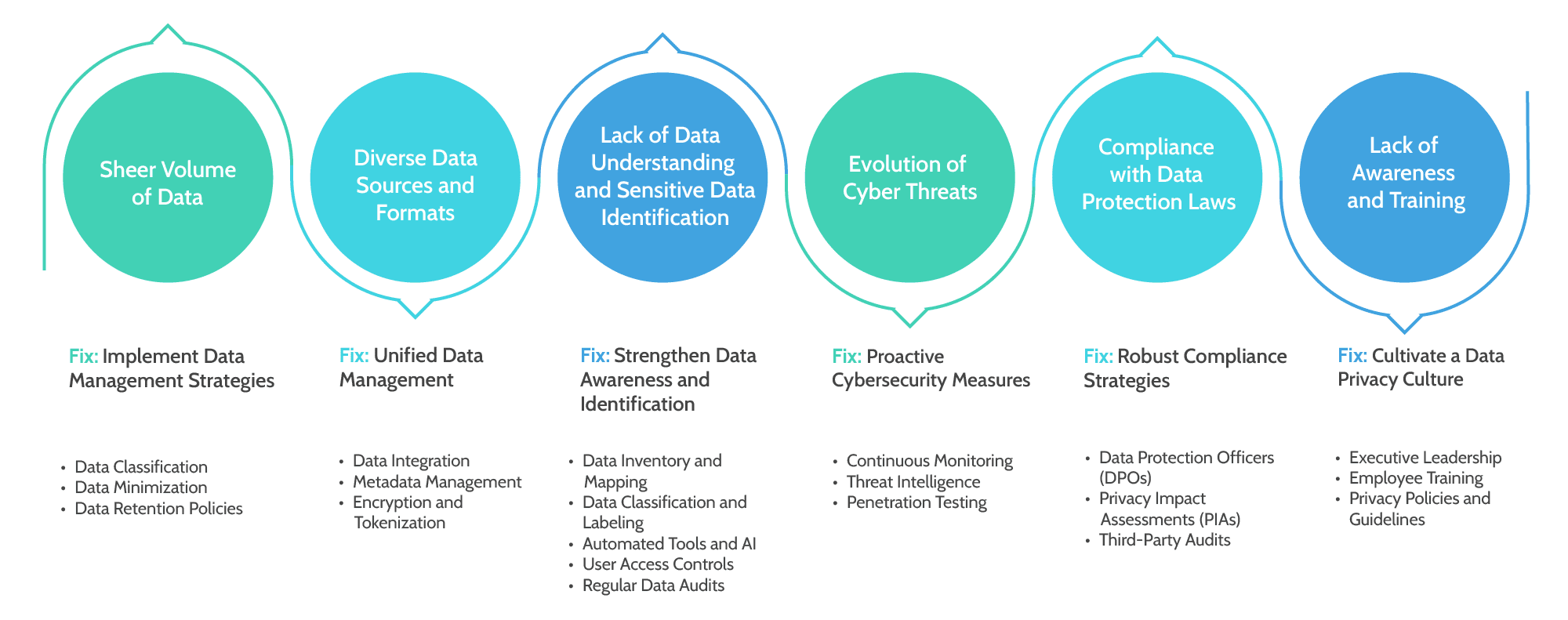

1. Sheer Volume of Data: Can you believe the amount of data organizations deal with these days? It’s mind-boggling! According to Statista, the global data volume is projected to reach a staggering 175 zettabytes by 2025. That’s like trying to handle an ocean of information! With so much data pouring in from various sources, it becomes tricky for organizations to keep track of all the PII they collect. For instance, in one of the largest data breaches in history, Yahoo suffered a series of attacks, exposing sensitive information of over 3 billion user accounts. The sheer volume of data stored on Yahoo’s servers made it challenging for the company to detect and respond to the breach promptly. The attackers exploited this massive data pool to gain unauthorized access, highlighting the need for robust data management strategies to handle vast amounts of information securely.
Fix: Implement Data Management Strategies
- Data Classification: Organizations should classify data based on sensitivity levels. By identifying PII within the vast data pool, they can prioritize its protection, reducing the risk of unauthorized access.
- Data Minimization: Adopt a “less is more” approach and only collect necessary data. Reducing the volume of collected PII minimizes the risk exposure and simplifies management.
- Data Retention Policies: Establish clear data retention policies to dispose of PII that is no longer needed, reducing the overall data burden.
2. Diverse Data Sources and Formats: Data comes in all shapes and sizes. You’ve got structured data, unstructured data, data from social media, emails, spreadsheets, and whatnot! It’s like trying to assemble a puzzle with pieces from different sets. A study by Experian found that 88% of organizations faced difficulties in managing unstructured data effectively. Also, here’s an example explaining the magnitude of this problem. Marriott International experienced a massive data breach that lasted for several years, affecting approximately 500 million guests. The breach involved data from various sources, including hotel reservations, loyalty programs, and payment systems, resulting in unauthorized access to PII. The diverse data sources and formats made it difficult for Marriott to detect and correlate the breach across its vast network, emphasizing the importance of unified data management practices.
Fix: Unified Data Management
- Data Integration: Utilize data integration tools to consolidate and unify data from various sources, making it easier to manage and analyze PII.
- Metadata Management: Establish effective metadata management practices to better understand the content and context of the data, facilitating accurate PII identification.
- Encryption and Tokenization: Apply encryption and tokenization techniques to protect sensitive data, regardless of its format or location.
3. Lack of Data Understanding and Sensitive Data Identification: Organizations collect vast amounts of data, but they may not fully understand what type of data they have or which pieces are sensitive. It’s like having a treasure trove of information but not knowing which jewels are the most valuable! Without a clear understanding of the data they hold, organizations can’t effectively prioritize and protect the most sensitive information, including PII. A study conducted by the International Association of Privacy Professionals (IAPP) found that 60% of organizations struggled to inventory and map personal data accurately. This lack of data understanding can leave gaps in their protection strategies, making it easier for PII to slip through the cracks. Uber faced a significant data breach in 2016 where hackers gained access to the PII of 57 million riders and drivers. Instead of disclosing the breach to affected individuals and authorities, Uber decided to pay the hackers to keep it quiet. This incident exposed Uber’s lack of data understanding and failure to identify the severity of the breach promptly. The lack of awareness about the importance of timely disclosure and the gravity of the breach tarnished Uber’s reputation and led to legal penalties.
Fix: Strengthen Data Awareness and Identification
- Data Inventory and Mapping: Create a comprehensive data inventory, including all data repositories and their contents. Mapping data flows helps identify where PII is stored, processed, or transferred, enabling better data governance.
- Data Classification and Labeling: Implement a data classification framework to categorize data based on sensitivity levels. Clearly label data containing PII so that employees can handle it appropriately.
- Automated Tools and AI: Leverage automated tools and AI-driven solutions to assist in data identification and classification tasks, streamlining the process and reducing human error.
- User Access Controls: Restrict access to sensitive data to only authorized personnel. Role-based access control (RBAC) ensures that employees can access PII only if necessary for their job responsibilities.
- Regular Data Audits: Conduct periodic data audits to assess the accuracy of data classification and ensure compliance with internal policies and data protection regulations.
4. Evolution of Cyber Threats: You know how hackers keep getting smarter and more sophisticated? It’s like playing a never-ending game of cat and mouse! According to Accenture, the average number of security breaches has increased by 11% since 2018. Remember the WannaCry ransomware attack that affected hundreds of thousands of computers globally, including healthcare institutions and government agencies? This cyber threat exploited a vulnerability in outdated software, encrypting users’ data and demanding ransom for its release. The rapid evolution of such ransomware attacks caught many organizations off guard, underscoring the need for proactive cybersecurity measures and regular updates to mitigate evolving threats.
Fix: Proactive Cybersecurity Measures
- Continuous Monitoring: Implement real-time monitoring of data systems to detect and respond to potential breaches promptly.
- Threat Intelligence: Stay informed about emerging cyber threats and vulnerabilities through threat intelligence services to proactively defend against attacks.
- Penetration Testing: Conduct regular penetration testing to identify vulnerabilities and address them before malicious actors exploit them.
5. Compliance with Data Protection Laws: Different countries have different data protection laws, and keeping up with all the regulations is no picnic. The European Union’s General Data Protection Regulation (GDPR) is one of the most well-known examples. A survey by TrustArc found that only 28% of companies believed they were fully GDPR compliant and sadly even the biggest global brands do not qualify. In fact, Google faced scrutiny under the European Union’s General Data Protection Regulation (GDPR) for its lack of transparency and user consent in personalizing ads. The French data protection authority CNIL imposed a fine of €50 million for violating GDPR requirements. This case demonstrated the challenges organizations face in complying with complex data protection laws, and the severe penalties for non-compliance, stressing the need for robust data protection and privacy compliance programs.
Fix: Robust Compliance Strategies
- Data Protection Officers (DPOs): Appoint DPOs to ensure compliance with relevant data protection laws and serve as a point of contact for regulatory authorities.
- Privacy Impact Assessments (PIAs): Conduct PIAs to evaluate and mitigate risks associated with processing PII, ensuring compliance from the outset.
- Third-Party Audits: Regularly conduct third-party audits to assess and validate compliance efforts and identify areas for improvement.
6. Lack of Awareness and Training: Sometimes, it’s not that organizations don’t care about PII management; it’s just that they aren’t fully aware of its importance. A PwC study revealed that 37% of companies didn’t have an executive who was responsible for privacy and data protection. Without proper leadership and training, it’s tough to stay on top of PII protection. As an instance, Equifax, one of the largest credit reporting agencies, experienced a massive data breach that exposed sensitive information of 147 million individuals. The breach occurred due to a vulnerability that Equifax failed to patch promptly. This incident highlighted the lack of awareness and adequate training within the organization regarding the significance of timely security updates and data protection measures.
Fix: Cultivate a Data Privacy Culture
- Executive Leadership: Appoint an executive responsible for privacy and data protection to champion the cause and allocate necessary resources.
- Employee Training: Conduct regular data privacy training for all staff members, emphasizing the significance of PII protection and the potential consequences of mismanagement.
- Privacy Policies and Guidelines: Develop and enforce comprehensive privacy policies and guidelines to set clear expectations for employees regarding PII handling.
Empowering Data Democratization through Efficient PII Management
As an onset of demand for efficient PII management, data democratization has emerged as a critical concept in the digital age. In today’s data-driven world, data has immense value, and individuals should have a say in how their data is used and shared. It’s crucial for building trust with companies and organizations. When you know what they’re doing with your data, it’s easier to trust them with it. Recent surveys show that nearly 80% of consumers are more likely to trust a company if they’re transparent about their data practices. So, data democratization is a win-win for everyone! Here’s why data democratization matters:
- Transparency and Trust: When individuals have access to their data and understand how it’s used, it fosters transparency. Trust between individuals and organizations increases when data practices are clear and understandable.
- Informed Decision-Making: Data democratization empowers individuals to make informed choices about sharing their data. They can assess the benefits and risks of data sharing, ensuring that their data is used in ways that align with their preferences and values.
- Personalization and Customization: By allowing individuals to control their data, organizations can deliver personalized and relevant services. Data democratization enables customized experiences while respecting individual boundaries.
- Empowering Innovation: When individuals have control over their data, they are more likely to participate in data-sharing initiatives for research and innovation. This participation fuels data-driven advancements while respecting individual consent.
- Ethical Data Practices: Data democratization encourages organizations to adopt ethical data practices, such as data minimization and clear data usage policies. It places a focus on data protection and responsible data use.
- Reducing Data Misuse: Giving individuals control over their data can help prevent data misuse and unauthorized sharing. It creates a sense of responsibility among organizations to use data responsibly and ethically.
But hold on, there’s a catch – balancing data democratization with PII protection. It’s like walking on a tightrope – you want to share your data for better services, but you also want to ensure it’s safe and sound. Striking the right balance is essential to protect your privacy while still enjoying the perks of data-driven services.
- Ensuring Consent: While data democratization aims to empower individuals, it must ensure that consent is obtained before data is shared or processed. Organizations must uphold strict data governance to avoid violating privacy rights.
- Data Minimization: Data democratization should not lead to excessive data collection. Organizations should focus on collecting only the necessary data and avoid retaining data for longer than required.
- Secure Data Management: Organizations must maintain robust security measures to protect individual data. Strong encryption and access controls are crucial to safeguard against data breaches and unauthorized access.
- Educating Users: For data democratization to succeed, individuals must be educated about their rights and how to exercise control over their data. Organizations should provide clear information about data practices and how individuals can manage their data.
So, how do organizations manage all this data responsibly? Well, that’s where comprehensive data management and best practices come into play. It’s like organizing a cluttered room – you need to have a system in place. Responsible data collection and storage, identifying, categorizing & controlling access to sensitive information, and disposing of data properly are all part of the game.
The Data Dynamics Advantage
Introducing the cutting-edge Data Dynamics Unified Data Management Platform, an acclaimed software solution designed to empower organizations with comprehensive insights into their PII data landscape and enable effective risk mitigation. This award-winning platform incorporates four key modules – Data Analytics, Mobility, Security, and Compliance – and has garnered success across 300 organizations, including renowned manufacturing enterprises like 28 Fortune 100 companies.
This revolutionary platform leverages state-of-the-art technology to simplify the process of discovering, classifying, tagging, and indexing sensitive or private information within unstructured data files. By seamlessly filtering sensitive data from unstructured content, organizations can ensure the protection of valuable information, maintain regulatory compliance, and foster trust among customers and stakeholders. This invaluable capability allows for the transformation of unstructured data into refined and structured formats, facilitating deep data analytics, risk reduction, data privacy, and data protection.
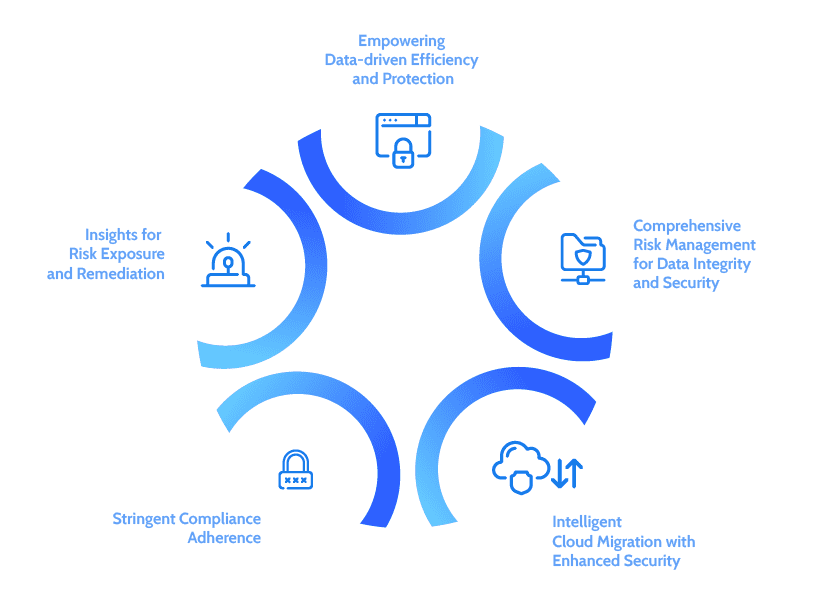

- Empowering Data-driven Efficiency and Protection: Gain complete visibility and optimization of your data with robust file ownership tracking, creation timestamps, and file categorization based on sensitivity. Leverage metadata for informed decision-making, reduce security risks, and enhance data protection with tailored security measures.
- Insights for Risk Exposure and Remediation: Discover and classify sensitive data using AI/ML and NLP-driven content analytics. Access actionable insights through advanced analytics, isolate high-risk data in secure storage, and improve open share security. Achieve comprehensive data protection, governance, and risk management.
- Stringent Compliance Adherence: Classify data with industry-standard templates, ensure reliable internal governance reporting with blockchain technology, and scale the solution to accommodate evolving regulatory requirements.
- Intelligent Cloud Migration with Enhanced Security: Streamline cloud adoption with risk-aware automated migration, fortify security measures, implement intelligent tiering and placement for cost efficiency, and enable secure data sharing while adhering to privacy regulations. Scale effortlessly and maintain compliance in multi-cloud environments.
- Comprehensive Risk Management for Data Integrity and Security: Take a holistic approach with data analytics, real-time insights, automation, and enhanced security to address risk and compliance challenges. From file access monitoring to metadata analysis, ensure adherence to regulatory requirements and preserve data integrity.
To discover more about how Data Dynamics can help you, please visit www.datadynamicsinc.com or contact us at solutions@datdyn.com / (713)-491-4298 / +44-(20)-45520800.