The CISO’s role has always been safeguarding an organization’s digital world but how do you secure what you can’t see, organize what doesn’t fit, and govern what seems uncontrollable? This is the dilemma today’s Chief Information Security Officers (CISOs) face as unstructured data grows at an unprecedented scale. Here are some alarming facts that will undoubtedly make any CISO’s hair stand on end.
Unstructured data now makes up 80-90% of all data generated by organizations (IDC).
With 30% of this data deemed sensitive or critical (Gartner), it’s a ticking time bomb for security.
But why is managing unstructured data so critical for CISOs?
Visibility Gaps: You can’t secure what you can’t see. Legacy tools are ill-equipped to locate, classify, and monitor unstructured data spread across on-prem systems, cloud platforms, and endpoints.
Increased Risks: 63% of data breaches are linked to unstructured data sources with phishing attacks, ransomware, and insider threats targeting the weakest links.
Regulatory Pressure: Compliance with GDPR, HIPAA, and CCPA now requires stricter governance over sensitive unstructured data, with non-compliance fines skyrocketing by 40% over the last two years (DLA Piper).
CISOs at a crossroads?
The evolving landscape of data security demands that CISOs move beyond the traditional “protect thy perimeter” model. Remote workforces, multi-cloud environments, and AI-powered tools have scattered sensitive information across hybrid ecosystems, introducing unprecedented complexity. This decentralization of data storage and access calls for a strategic shift in how unstructured data is managed, secured, and governed.
- Dynamic Data Mapping and Risk Profiling
Instead of simply discovering hidden sensitive data, modern solutions must map unstructured data dynamically and continuously assess its risk profile. For example, AI/ML-powered tools can evaluate access patterns, user behavior, and regulatory applicability in real time. This enables CISOs to prioritize interventions where risks are highest, reducing blind spots and ensuring ongoing compliance.
- Criticality-Informed Security Architecture
Classification alone isn’t enough. CISOs need context-aware tools that embed data criticality into security architecture dynamically. For instance, identifying whether a dataset is tied to operational continuity, high-value IP, or compliance mandates can trigger tailored responses like adaptive encryption, automated backups, or real-time anomaly detection. This ensures limited resources are directed where they matter most.
- Behavioral Policy Automation
Rather than relying on static policies, CISOs should enforce behavioral policy automation. Access controls, encryption mechanisms, and retention policies should adapt to real-time events, such as unusual user activity or geographic shifts in access patterns. This proactive governance ensures that security evolves alongside threats while maintaining compliance with regulatory changes.
The question is: How can they turn the liability of unstructured data into a strategic advantage? Here are five key strategies to address the chaos of unstructured data and emerge stronger in the process.
Five Cutting-Edge Strategies for the 2025 CISO Playbook to Tame Unstructured Data Chaos
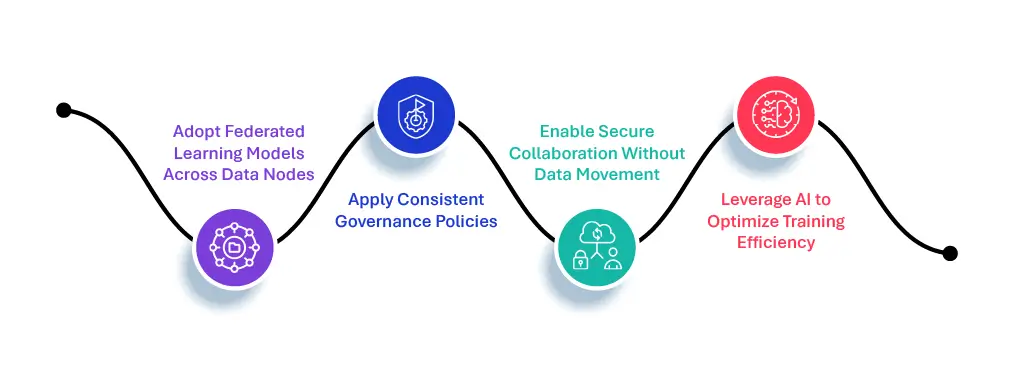
1. Harness Federated Learning for Data Security
Why it’s important: Traditional centralized data management exposes sensitive information during transfers and aggregations. Federated learning enables AI-driven insights at the data source, ensuring sensitive information never leaves its origin.
What must be done:
- Adopt Federated Learning Models Across Data Nodes: Federated learning frameworks allow distributed training of machine learning models directly on unstructured data repositories. AI orchestration capabilities ensure seamless implementation across hybrid and multi-cloud environments.
- Apply Consistent Governance Policies: Policy-driven architecture enforces data governance across distributed nodes. This ensures that each data source complies with security and privacy regulations.
- Enable Secure Collaboration Without Data Movement: Metadata contextualization tools prepare unstructured data for federated learning, extracting actionable insights without exposing sensitive information.
- Leverage AI to Optimize Training Efficiency: AI algorithms dynamically adjust model training based on resource availability and compliance needs, ensuring efficiency and privacy adherence.
How it helps:
Federated learning allows organizations to harness the power of AI without risking data exposure or breaching regulatory compliance. This supports business growth by enabling data-driven innovation in highly regulated industries like finance and healthcare, all while reducing the costs and risks of centralized data processing. CISOs can simultaneously enhance security and accelerate the adoption of AI-driven initiatives.
2. Build AI-Driven Data Contamination Filters
Why it’s important: Contaminated data—whether corrupted, biased, or redundant—can sabotage AI models, analytics, and decision-making. Proactively detecting and isolating such data safeguards downstream operations and ensures data reliability.
A study found that a version of GPT-2 scored 15% points higher when tested on a benchmark that had seeped into its training data versus a benchmark that it had never seen before, highlighting the risk of data contamination.
What must be done:
- Deploy Advanced AI Models for Anomaly Detection: AI-powered anomaly detection scans vast unstructured datasets for inaccuracies and potential contamination in real-time.
- Monitor Data Integrity During Ingestion: Real-time ingestion monitoring tools to validate data before it enters storage or analytics workflows, ensuring only clean data is processed.
- Leverage Metadata Intelligence for Contamination Prevention: Metadata-driven intelligence automates classification and tagging to isolate problematic files, preventing contamination from spreading across systems.
- Establish Data Quality Dashboards: Federated data management dashboards help visualize the state of data quality, enabling informed decisions to resolve contamination risks swiftly across the breadth of an organization.
How it helps:
AI-driven contamination filters prevent cascading failures caused by bad data, reducing the risk of faulty business decisions and reputational damage. This strengthens the reliability of AI systems and analytics, giving CISOs the ability to position their organizations as leaders in precision-driven innovation while mitigating compliance risks.
3. Embrace Data-Centric Security with Adaptive Decryption
Why it’s important: Static encryption models create inefficiencies when unstructured data needs to be dynamically shared. Adaptive decryption provides secure yet agile data access, vital for modern workflows.
IBM’s Cost of a Data Breach Report estimates that it takes 287 days to detect and contain a data breach caused by substandard encryption in 2021.
What must be done:
- Implement Granular Access Controls: Context-aware access controls adjust decryption dynamically based on user roles, device security, and location.
- Incorporate Behavior-Based Decryption Rules: A behavioral analytics engine refines permissions dynamically, granting access based on real-time risk profiles.
- Deploy Real-Time Encryption Audits: Monitor decryption events continuously with role-based auditing, ensuring any unauthorized activity is immediately flagged and acted upon.
- Automate Policy Management: Automated workflows enforce scalable decryption policies that adapt to the organization’s growing unstructured data needs without compromising security.
How it helps:
Adaptive decryption eliminates delays caused by static security models, enabling faster, more secure collaboration. It supports digital transformation by ensuring that operational speed and security are not competing priorities. CISOs gain the ability to drive business agility while maintaining robust security postures, a critical advantage in fast-moving industries.
4. Use Synthetic Data for Risk-Free Collaboration
Why it’s important: Sharing unstructured data for analytics or innovation introduces privacy risks and regulatory complexities. Synthetic data offers a secure alternative, allowing organizations to leverage the value of sensitive datasets without exposing them.
The synthetic data generation market size was valued at USD 288.5 million in 2022 and is projected to grow to USD 2,339.8 million by 2030.
What must be done:
- Integrate Synthetic Data Generation Tools: Data masking and anonymization capabilities create synthetic datasets that retain statistical properties while removing identifiable information.
- Automate Data Preparation Workflows: Self-service unstructured data management software enables teams to independently generate synthetic datasets, speeding up innovation cycles.
- Ensure Compliance with Lineage Tracking: Data Lineage tracking capabilities provide visibility into how synthetic datasets are derived and used, ensuring audit readiness.
- Leverage AI for Synthetic Data Optimization: AI-powered engines can optimize synthetic data generation, ensuring that it accurately represents the characteristics of the original data for better analytics and machine learning outcomes.
How it helps:
Synthetic data unlocks the ability to innovate and collaborate without regulatory or privacy concerns. This positions CISOs as enablers of secure partnerships, accelerating time-to-market for new solutions while maintaining full compliance. It also reduces legal risks, freeing resources for growth-focused initiatives.
5. Leverage Quantum-Safe Cryptography for Long-Term Data Integrity
Why it’s important: As quantum computing evolves, traditional encryption methods will become obsolete. Future-proofing cryptographic strategies ensure long-term data security and safeguards against emerging threats.
The global quantum cryptography market size is projected to grow from USD 1157 million in 2024 to USD 7,594 million by 2030.
What must be done:
- Transition to Quantum-Resilient Encryption Algorithms: Encryption management capabilities to facilitate seamless adoption of quantum-safe standards, protecting data against future quantum risks.
- Centralize Encryption Policy Enforcement: Policy-driven encryption frameworks to enforce quantum-safe standards consistently across environments.
- Streamline Key Management for Quantum-Safe Security: Encryption key management tools ensure organizations maintain control during transitions to quantum-resilient models.
- Automate Cryptographic Updates: Automated workflows enable seamless upgrades to encryption algorithms, ensuring that security evolves alongside technology.
How it helps:
Adopting quantum-safe cryptography future-proofs the organization’s data infrastructure, ensuring its ability to withstand emerging threats. This positions CISOs as proactive leaders in risk management and technology adoption, strengthening stakeholder confidence and securing the organization’s competitive edge in an increasingly interconnected and vulnerable global landscape.
The Path Forward for CISOs
As we look ahead to 2025 and beyond, the role of the CISO is transforming from a traditional security gatekeeper to a strategic visionary, balancing innovation with the critical task of safeguarding the organization. The explosion of unstructured data, coupled with the proliferation of hybrid and multi-cloud environments, has created unprecedented challenges in visibility, governance, and security. Meanwhile, regulatory landscapes are becoming increasingly stringent, with new privacy and data sovereignty laws demanding proactive compliance measures. Emerging technologies like AI and quantum computing are further reshaping threat vectors, requiring CISOs to anticipate and mitigate risks that are still on the horizon. The modern CISO must navigate this complex ecosystem, ensuring that the organization’s data is not only secure but also positioned to deliver value through actionable insights and seamless collaboration.
This is where software like Zubin exemplifies the evolution of data management for the modern CISO. Designed with an AI-driven foundation, Zubin offers the ability to contextualize unstructured data across vast, hybrid landscapes, making it possible to transform raw information into actionable intelligence. Its metadata-driven approach enables granular control, allowing CISOs to enforce security, compliance, and access policies dynamically. Beyond tactical execution, Zubin’s self-service architecture empowers data creators and application owners to take charge of their data, decentralizing governance while maintaining centralized oversight. This balance between autonomy and control makes Zubin an ideal partner in building secure, compliant, and agile organizations, positioning CISOs not just as protectors, but as enablers of innovation and strategic growth. To know more about Zubin, visit – https://www.datadynamicsinc.com/.
Sources:
IBM’s Cost of a Data Breach Report estimates that it takes 287 days to detect and contain a data breach caused by substandard encryption in 2021.
The synthetic data generation market size was valued at USD 288.5 million in 2022 and is projected to grow to USD 2,339.8 million by 2030.
The global quantum cryptography market size is projected to grow from USD 1157 million in 2024 to USD 7,594 million by 2030.






